The question comes up pretty often. Is Epicor FDA compliant? Can we use the corrective action system in Epicor or what? Is the DMR process ok or do I have to keep doing it on paper? The answer out of the box is no, everything has to be done on paper.
FDA Part 11 has a requirement where if the record of an activity is recorded, a password must be provided. If a user has to record 5 activities, when they make each record a password must be given. A person should not be able to log in with their password once, make 5 records with no password prompt, then log out. The worry is that a different person could walk up to the terminal and start approving stuff under the user’s name.
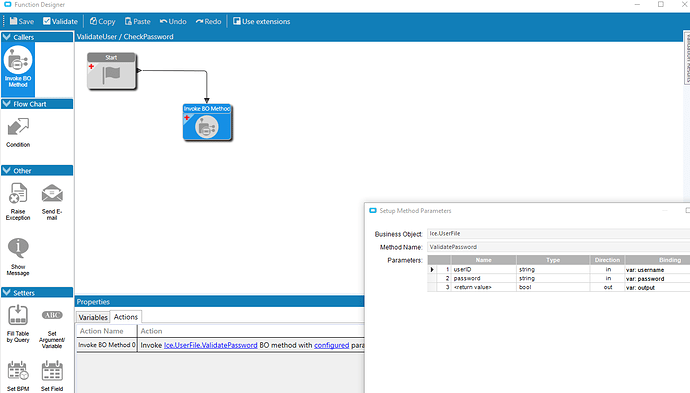
In order to make a record, the FDA needs to know who signed what, and when (usually date only). We can use a BPM to write the current user ID to a custom field and the date to another field. That part is simple. The password requirement is the hard part but with the advent of Data Masking in 10.2.300 it gets much simpler. Since the QA department wanted to ditch their antique access database and paper record system, I thought I’d give it a try.
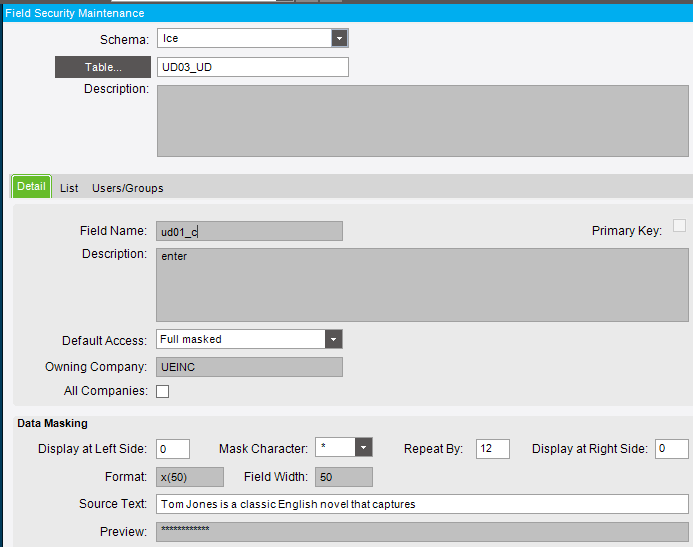
I wanted to create a custom field on the User table and use it to store the FDA password but it’s a huge pain setting anything like that up on that table so I just used one of the UD tables, UD03.
Key 1 is the user ID and the intentionally obscurely named ud01_c will store the corresponding user’s FDA password.
In Field Security Maintenance, I enabled Data Masking on that field.
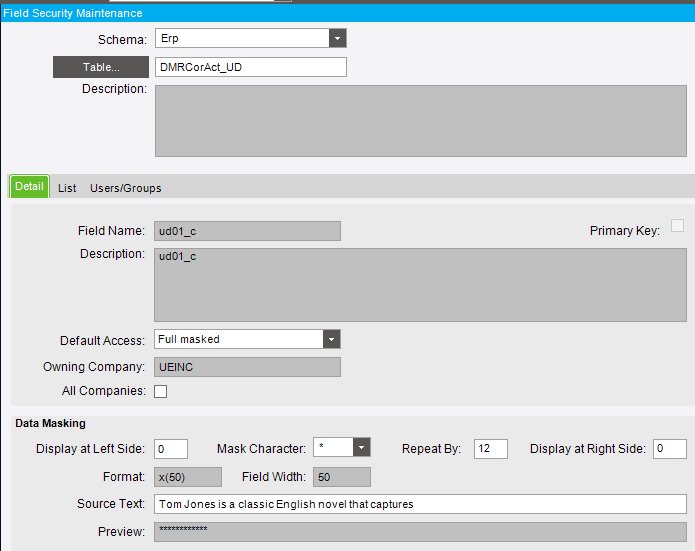
For corrective actions, I created a matching custom field on DMRCorAct_ud and applied the same Data Masking.
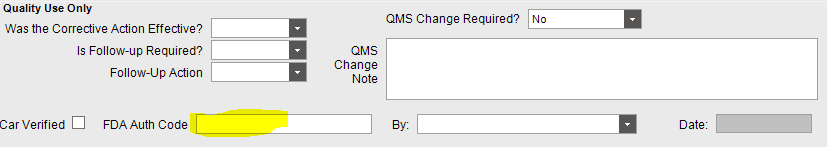
I have a heavily customized form for corrective actions. in the verification area, there is a field for the user to click ‘CAR Verified’ and enter their FDA Authorization code. For non-security manager users the code field will always just display asterisks.
Upon save, an In-Transaction Data Directive on DMRCorAct will do the following:
-
If the verify box is changed from false to true (this is a custom field) then proceed.
-
Make sure user is in the CAR Managers security group, an extra level of security.
-
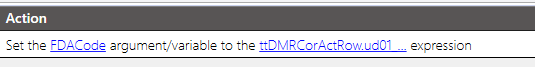
Set the FDACode variable to what the user entered.
-
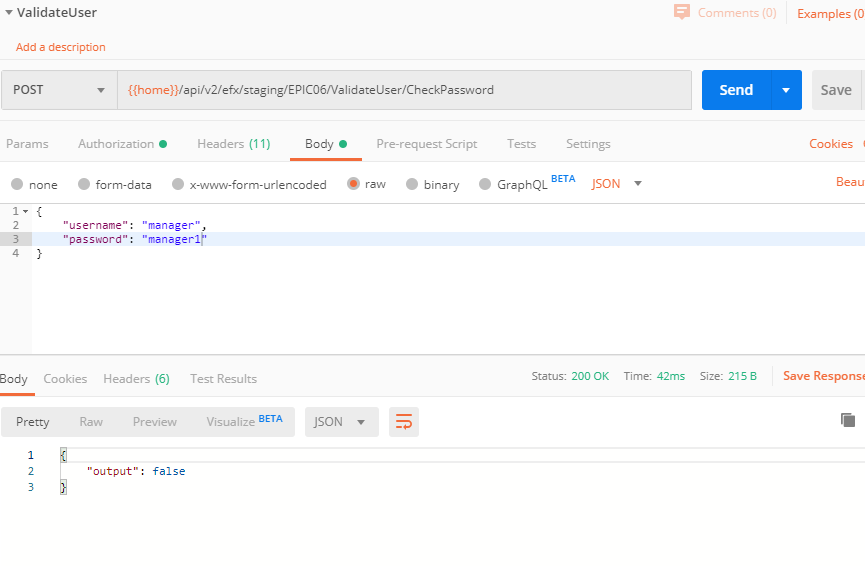
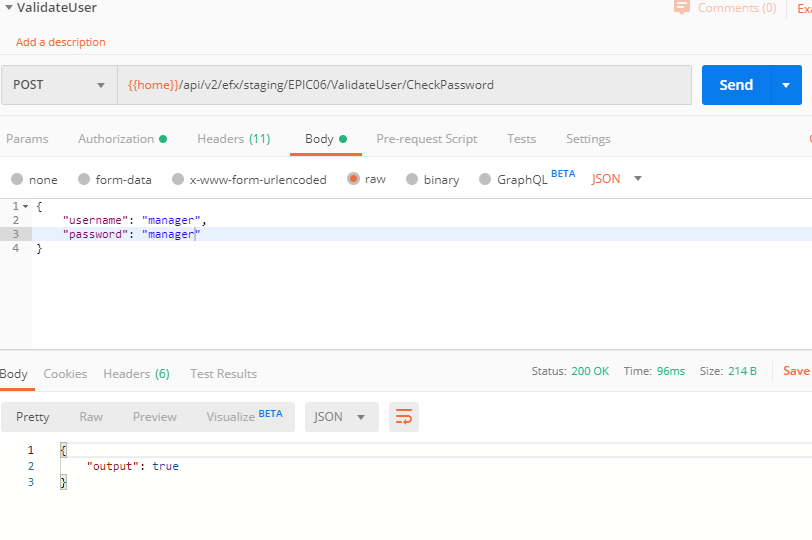
By query, make sure the FDA code the user entered matches the one for the current user on table UD03.
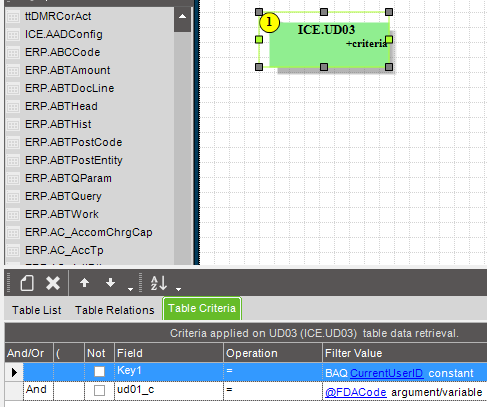
-
Check for completeness of the form (previous steps marked complete)
-
Writes the current user ID to a custom verified by field.
-
Sets ttDMRCorAct.AuditDt field of the changed row to the DateTime.Now expression (this will close the corrective action in the system will make the form read only using Epicor built in functionality)
-
Clear the FDA code from ttDMRCorAct, there is no reason to save it.
As long as testing this functionality is part of a controlled software validation protocol, there should be no reason to reject this methodology by ISO or GMP auditors.