<HUGE Safe Harbor here as this is for education in general to understand background of how E10 is put together and to be used for diagnostics purposes. If you call up for support on an aspect of this, you are likely to get limited to no help. Also beyond a few areas, this is possible (likely) to change!>
Scared off everyone now? Good, now on to the details.
I spent some time looking thru where we are at the moment. NOTE - this is a dump against an internal 10.2.300 build but I think these are all live in 10.2.200 (see safe harbor up top, right?).
First, many may be asking - what’s a header? Logically it’s just a string variable that is a two way pipe on every call client to server and server to client. Http, heck Tcp, has this ability so E10 simply leverages it to pass some data around to do it’s work without polluting every method call.
So here they are:
Let’s go thru some items in here…
First, note a fair amount of reserved ones. I am calling them reserved from my point of view (see the safe harbor above). I don’t see the value of exposing them when we have better ways to deal with log traces for example.
Next, let’s iterate thru the rest these quickly top to bottom-
-
License - This is used to tell the server which license type the client would prefer to consume. Note the way I stated that. Biz Logic from Marketing is obviously in charge and has final say
 The Guid value is the equivalent of what you see in Admin Console Sessions. These values are what you see in your lic files is you want to look up the values:
The Guid value is the equivalent of what you see in Admin Console Sessions. These values are what you see in your lic files is you want to look up the values:
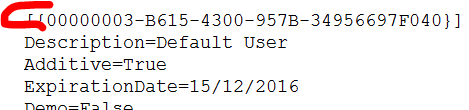
-
CallSettings - I wish this had been named Session Override or something similarly badly named. These values override what you usually think of in Session as you navigate thru the software. Note that not all Session variables are visible and exposed. Some for good reasons, some because no one has asked for it. We are adding more of these as we find the need internally on projects like Mobile CRM.
-
ContextHeader - The BPM payloads you see in BPM all the time
-
AuthTokenHeader - The authentication token obtained from the legacy ERP token server
-
AzureADToken - The authentication token obtained from Azure AD
-
OnBehalfOfToken - The name this agent is acting on behalf of. For example, this could be a call from the Task Agent that is printing a report for someone else. ‘On Behalf of’ another user. The agent account running this needs the ‘impersonation’ right in User Maintenance.
-
SessionInfo - This is the Guid that points at the server side ‘Session’ data stored in the app server to hold the state of the client to server ‘session saga’ information. EmployeeID, Workstation, User, license consumed and so on. Since not everything is exposed via ContextHeader above, you sometimes need to start a server session, grab the ID and have the server track the state of your navigation thru the software.
There you go, brain dump done. Questions?
